
Simply navigate to the main hard drive on which Windows is installed, right-click and select properties as follows:
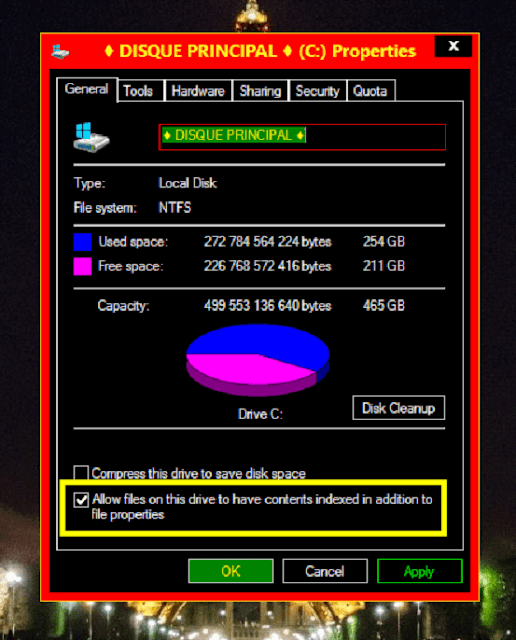
You'll notice below an option:
allow files on this drive to have contents indexed in addition to file properties
It may be enabled by default as it is for me, and may not be, in this case activate it because this feature is very useful as it enables you to search within the content of the files and not only its properties, for example, to search for a Word file called article. You can use the name - article- or-word-, space, date of creation and other properties. However, when you enable this property type
You can search for a file not only by using properties, but also by using content. For example, if you have a very large number of Word files and forget the name of the file you want, you will be able to search for it by searching for a word or phrase that you remember well. The subject in the file, for example. To draw you closer to the picture, I assume you are a math teacher and I have prepared a lesson called root lesson. The file was named cours43.word, but over time I forgot the file title due to the accumulation of lessons I have prepared. So thanks to this feature that you must activate in the hard drive, you will be able to find the file required only by entering the title of the lesson, which is - the lesson of the root numbers -.
This is a very simple example to give you closer to the picture. You can use the technique in more professional ways by searching within xml web pages, patches, and other files that can hide very sensitive information that you do not need to access. That professional hackers rely on this technique to facilitate the search process and extract some sensitive information hidden files.
♦ ♦ ♦ ♦ ♦.
Now you can only share your opinion on the subject of the day below in the comments, and do not forget that we are here to answer any question you may have about using this technology.




0 Comments